|
IP Masquerade is a networking function in Linux similar to the one-to-many (1:Many) NAT (Network Address Translation) servers found in many commercial firewalls and network routers.
A D V E R T I S E M E N T
For example, if a Linux host is connected to the Internet via PPP, Ethernet, etc., the IP Masquerade feature allows other "internal" computers connected to this Linux box (via PPP, Ethernet, etc.) to also reach the Internet as well. Linux IP Masquerading allows for this functionality even though these internal machines don't have an officially assigned IP address.
MASQ allows a set of machines to invisibly access the Internet via the MASQ gateway. To other machines on the Internet, the outgoing traffic will appear to be from the IP MASQ Linux server itself. In addition to the added functionality, IP Masquerade provides the foundation to create a HEAVILY secured networking environment. With a well built firewall, breaking the security of a well configured masquerading system and internal LAN should be considerably difficult to accomplish.
Please DO NOT confuse routers with firewalls and the performance of
IP masquerading. The commands that allow IP masquerading are a simple
form of a firewall, however routing is a completely different function,
as described previously. Setting a computer up to act as a router is
completely different than setting up a computer to act as a firewall.
Although the two functions are similar in that the router or firewall
will act as a communication mechanism between two networks or subnets,
the similarity ends there. A computer can be either a router or a
firewall, but not both. If you set up a computer to act as both a router
and a firewall, you have defeated the purpose of your firewall!
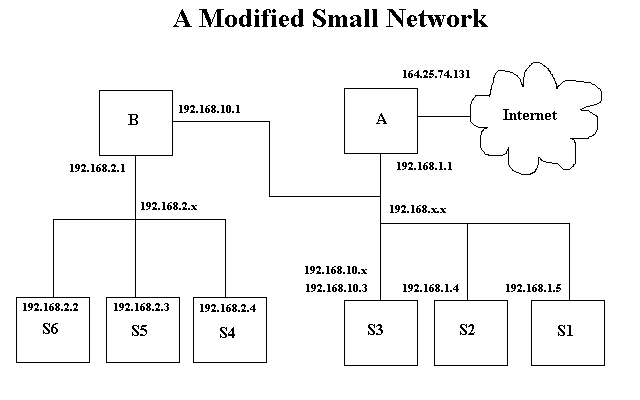
If you refer to the diagram below, the machines on network
192.168.2.x will obtain services through gateway B using IP
masquerading, when gateway B is setup properly. What basically happens
when IP masquerading is set up on gateway B is described in the
following example. If machine S6 tries to ping S2, its ping packages
will be wrapped in a package for its default gateway, gateway B, because
S6 knows by its netmask that S2 in on another network. When gateway B
receives the packages from S6, it converts them to ping packages as
though they were sent from itself and sends them to S2. As far as S2 can
tell, gateway B has pinged it. S2 receives the packages and responds to
gateway B. Gateway B then converts the packages to be addressed to S6
and sends them. This is why it is called IP masquerading, since gateway
B masquerades for machines S4, S5, and S6. Machines S1 through S3 and
gateway A cannot initiate any communication with S4 through S6. In fact
they have no way to know that those machines even exist!
IP masquerading allows internal machines that don't have an officially
assigned IP addresses to communicate to other networks and especially the
internet. In Linux, IP masquerading support is provided by the kernel. To get it
to work you must do essentially three things:
- Be sure the kernel has support for IP masquerading.
- Be sure modules needed for support are loaded into the kernel.
- Set up the firewall rules.
For complete information on the setup of IP masquerading, see the following
Linux how-tos:
- IPCHAINS-HOWTO
- Firewall-HOWTO
- IP-Masquerade-HOWTO
Some of the information in this section is based on these how-tos. This
section summarizes and puts in simple steps some of the items you will be
required to perform to set up IP masquerading. It is not a replacement for the
Linux how to documents, but a complement to them by giving an overview of what
must be done. You may access the howtos from one of the websites listed in the
Linux websites section. The Linux Documentation Project or Metalab's
Index of Linux publications will have copies if these howtos.
To set up IP masquerading in Linux you must first be sure your kernel
supports IP masquerading with the following options set (This is for a 2.2.x
kernel or higher):
Prompt for development and/or incomplete code/drivers (CONFIG_EXPERIMENTAL)
[Y/n/?]- YES
Enable loadable module support (CONFIG_MODULES) [Y/n/?] - YES
Networking support (CONFIG_NET) [Y/n/?] - YES
Packet socket (CONFIG_PACKET) [Y/m/n/?] - YES
Kernel/User netlink socket (CONFIG_NETLINK) [Y/n/?] - YES
Routing messages (CONFIG_RTNETLINK) [Y/n/?] - NO
Network firewalls (CONFIG_FIREWALL) [Y/n/?] - YES
TCP/IP networking (CONFIG_INET) - YES
IP: advanced router (CONFIG_IP_ADVANCED_ROUTER) [Y/n/?] - NO
IP: verbose route monitoring (CONFIG_IP_ROUTE_VERBOSE) [Y/n/?] - YES
IP: firewalling (CONFIG_IP_FIREWALL) [Y/n/?] - YES
IP: firewall packet netlink device (CONFIG_IP_FIREWALL_NETLINK) [Y/n/?] - YES
IP: always defragment (required for masquerading) (CONFIG_IP_ALWAYS_DEFRAG)
[Y/n/?] - YES
IP: masquerading (CONFIG_IP_MASQUERADE [Y/n/?] - YES
IP: ICMP masquerading (CONFIG_IP_MASQUERADE_ICMP) [Y/n/?] - YES
IP: masquerading special modules support (CONFIG_IP_MASQUERADE_MOD) [Y/n/?] -
YES
IP: ipautofw masquerade support (EXPERIMENTAL) (CONFIG_IP_MASQUERADE_IPAUTOFW)
[Y/n/?] - NO
IP: ipportfw masq support (EXPERIMENTAL) (CONFIG_IP_MASQUERADE_IPPORTFW) [Y/n/?]
- YES
IP: ip fwmark masq-forwarding support (EXPERIMENTAL) (CONFIG_IP_MASQUERADE_MFW)
[Y/m/n/?] - NO
IP: optimize as router not host (CONFIG_IP_ROUTER) [Y/n/?] - YES
IP: GRE tunnels over IP (CONFIG_NET_IPGRE) [N/y/m/?] - NO
IP: TCP syncookie support (not enabled per default) (CONFIG_SYN_COOKIES) [Y/n/?]
- YES
Network device support (CONFIG_NETDEVICES) [Y/n/?] - YES
Dummy net driver support (CONFIG_DUMMY) [M/n/y/?] - YES
/proc filesystem support (CONFIG_PROC_FS) [Y/n/?] - YES
These are the kernel options you need for IP Masquerade. You will need to select
other options for your specific hardware and network setup. Read the IP
masquerade and kernel howtos for more information. You may also want the section
about how to compile the Linux kernel on the Linux User's Guide in the Linux
section of this documentation.
Create the following text and place it in a file "/etc/rc.d/rc.firewall".
This will load your needed modules into your kernel and set up your basic
firewall rules. If you copy the file from this page, be sure to remove carriage
returns when you get it into Linux or it may not work properly.
# rc.firewall - Initial SIMPLE IP Masquerade setup for 2.0.x kernels using IPFWADM
#
# Load all required IP MASQ modules
#
# NOTE: Only load the IP MASQ modules you need. All current available IP MASQ modules
# are shown below but are commented out from loading.
# Needed to initially load modules
#
/sbin/depmod -a
# Supports the proper masquerading of FTP file transfers using the PORT method
#
/sbin/modprobe ip_masq_ftp
# Supports the masquerading of RealAudio over UDP. Without this module,
# RealAudio WILL function but in TCP mode. This can cause a reduction
# in sound quality
#
#/sbin/modprobe ip_masq_raudio
# Supports the masquerading of IRC DCC file transfers
#
/sbin/modprobe ip_masq_irc
# Supports the masquerading of Quake and QuakeWorld by default. This modules is
# for for multiple users behind the Linux MASQ server. If you are going to play
# Quake I, II, and III, use the second example.
#
#Quake I / QuakeWorld (ports 26000 and 27000)
#/sbin/modprobe ip_masq_quake
#
#Quake I/II/III / QuakeWorld (ports 26000, 27000, 27910, 27960)
# /sbin/modprobe ip_masq_quake ports=26000,27000,27910,27960
# Supports the masquerading of the CuSeeme video conferencing software
#
#/sbin/modprobe ip_masq_cuseeme
#Supports the masquerading of the VDO-live video conferencing software
#
#/sbin/modprobe ip_masq_vdolive
#CRITICAL: Enable IP forwarding since it is disabled by default since
#
# Redhat Users: you may try changing the options in /etc/sysconfig/network from:
#
# FORWARD_IPV4=false
# to
# FORWARD_IPV4=true
#
echo "1" > /proc/sys/net/ipv4/ip_forward
# Dynamic IP users:
#
# If you get your Internet IP address dynamically from SLIP, PPP, or DHCP, enable this following
# option. This enables dynamic-ip address hacking in IP MASQ, making the life
# with DialD, PPPd, and similar programs much easier.
#
echo "1" > /proc/sys/net/ipv4/ip_dynaddr
# MASQ timeouts
#
# 2 hrs timeout for TCP session timeouts
# 10 sec timeout for traffic after the TCP/IP "FIN" packet is received
# 160 sec timeout for UDP traffic (Important for MASQ'ed ICQ users)
#
/sbin/ipchains -M -S 7200 10 160
# DHCP: For people who receive their external IP address from either DHCP or BOOTP
# such as ADSL or Cablemodem users, it is necessary to use the following
# before the deny command. The "bootp_client_net_if_name" should be replaced
# the name of the link that the DHCP/BOOTP server will put an address on to?
# This will be something like "eth0", "eth1", etc.
#
# This example is currently commented out.
#
#
/sbin/ipchains -A input -j ACCEPT -i eth1 -s 0/0 67 -d 0/0 68 -p udp
# Enable simple IP forwarding and Masquerading
#
# NOTE: The following is an example for an internal LAN address in the 192.168.0.x
# network with a 255.255.255.0 or a "24" bit subnet mask.
#
# Please change this network number and subnet mask to match your internal LAN setup
#
/sbin/ipchains -P forward DENY
/sbin/ipchains -A forward -s 10.1.199.0/24 -j MASQ
Add the following line to the "/etc/rc.d/rc.local" file:
/etc/rc.d/rc.firewall
Of course the machines that you are configuring to be behind the machine
providing the masquerading service should be configured to use that as their
gateway. In this case S4 through S6 should use gateway B as their default
gateway.
|
